Navigating The Labyrinth: Understanding The Power Of Cyber Security Mind Maps
Navigating the Labyrinth: Understanding the Power of Cyber Security Mind Maps
Related Articles: Navigating the Labyrinth: Understanding the Power of Cyber Security Mind Maps
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Navigating the Labyrinth: Understanding the Power of Cyber Security Mind Maps. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Navigating the Labyrinth: Understanding the Power of Cyber Security Mind Maps
- 2 Introduction
- 3 Navigating the Labyrinth: Understanding the Power of Cyber Security Mind Maps
- 3.1 Decoding the Structure: A Visual Exploration of Cyber Security Elements
- 3.2 Beyond Visualization: The Practical Benefits of Cyber Security Mind Maps
- 3.3 FAQs: Addressing Common Questions About Cyber Security Mind Maps
- 3.4 Tips for Creating Effective Cyber Security Mind Maps
- 3.5 Conclusion: Navigating the Future with a Cyber Security Mind Map
- 4 Closure
Navigating the Labyrinth: Understanding the Power of Cyber Security Mind Maps
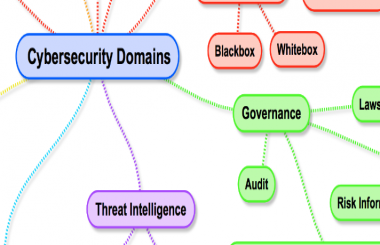
The digital landscape is a complex and ever-evolving terrain, riddled with threats and vulnerabilities. Navigating this terrain requires a comprehensive understanding of potential risks and effective mitigation strategies. This is where the power of a cyber security mind map shines.
A cyber security mind map is a visual representation of the intricate web of elements that constitute a robust security posture. It serves as a powerful tool for organizing, analyzing, and visualizing the complex interplay of threats, vulnerabilities, and countermeasures. This structured approach allows for a holistic understanding of the cyber security ecosystem, facilitating informed decision-making and effective risk management.
Decoding the Structure: A Visual Exploration of Cyber Security Elements
A typical cyber security mind map is built around a central theme, such as "Cyber Security Strategy" or "Threat Landscape." Branching out from this core are key concepts and their interconnections. For instance, a mind map focused on "Cyber Security Strategy" might feature branches like "Asset Identification," "Risk Assessment," "Security Controls," and "Incident Response." Each branch can be further subdivided, leading to a detailed and interconnected representation of the chosen theme.
Here are some common elements found within a cyber security mind map:
1. Assets: These are the critical resources that an organization needs to protect. This includes hardware, software, data, networks, and even human capital. Identifying and categorizing assets is the first step towards effective security planning.
2. Threats: These are the potential dangers that could harm an organization’s assets. Threats can be internal (e.g., disgruntled employees) or external (e.g., malicious hackers). Identifying and understanding the nature of threats is crucial for prioritizing security measures.
3. Vulnerabilities: These are weaknesses in an organization’s security infrastructure that can be exploited by threats. Vulnerabilities can be inherent in software, hardware, or even human behavior. Identifying and mitigating vulnerabilities is a key aspect of cyber security.
4. Security Controls: These are the mechanisms and policies implemented to protect assets from threats and vulnerabilities. Security controls can be technical (e.g., firewalls, intrusion detection systems), administrative (e.g., access control policies), or physical (e.g., locked doors, security cameras).
5. Incident Response: This refers to the plan and procedures for handling security incidents, including detection, containment, recovery, and post-incident analysis. A robust incident response plan is essential for minimizing damage and ensuring swift recovery.
6. Legal and Regulatory Compliance: This encompasses the legal and regulatory frameworks that govern cyber security practices within a specific industry or jurisdiction. Adhering to relevant regulations is crucial for mitigating legal risks and ensuring ethical data handling.
Beyond Visualization: The Practical Benefits of Cyber Security Mind Maps
The benefits of using a cyber security mind map extend beyond mere visualization. They offer a powerful framework for:
1. Comprehensive Risk Assessment: By visually mapping threats, vulnerabilities, and assets, organizations can gain a holistic view of their overall risk profile. This enables them to prioritize security measures based on the severity of potential threats and the value of affected assets.
2. Effective Policy Development: A mind map serves as a visual roadmap for developing comprehensive security policies. By outlining key security objectives, identifying relevant stakeholders, and defining roles and responsibilities, organizations can create a clear framework for implementing and enforcing security measures.
3. Enhanced Communication and Collaboration: The visual nature of mind maps facilitates clear and concise communication among security teams, IT personnel, and management. It allows for a shared understanding of security risks, mitigation strategies, and incident response procedures, fostering effective collaboration and efficient decision-making.
4. Streamlined Training and Education: Mind maps can be used to create engaging and informative training materials for employees at all levels. By visually representing key security concepts and best practices, organizations can effectively educate their workforce on cyber security awareness and responsible online behavior.
5. Continuous Improvement and Adaptation: The dynamic nature of the cyber security landscape necessitates continuous improvement and adaptation. Mind maps provide a flexible framework for regularly reviewing and updating security strategies in response to evolving threats and technological advancements.
FAQs: Addressing Common Questions About Cyber Security Mind Maps
1. Who can benefit from using a cyber security mind map?
Cyber security mind maps can be beneficial for individuals, organizations of all sizes, and even government agencies. Anyone involved in security planning, risk assessment, policy development, or incident response can leverage the power of mind mapping.
2. What are the different types of cyber security mind maps?
While the basic structure remains similar, mind maps can be customized to address specific needs. Some common types include:
- Threat Landscape Map: Focuses on identifying and classifying potential threats, analyzing their motives, and understanding their attack vectors.
- Vulnerability Assessment Map: Analyzes potential weaknesses in systems, applications, and processes, identifying vulnerabilities that could be exploited by threats.
- Security Control Map: Outlines the various security measures implemented to protect assets, including technical, administrative, and physical controls.
- Incident Response Map: Defines the procedures for handling security incidents, from detection and containment to recovery and post-incident analysis.
3. How can I create a cyber security mind map?
Creating a cyber security mind map involves a structured approach:
- Define the Scope: Clearly define the purpose and focus of the mind map.
- Central Theme: Identify the central theme or problem you want to address.
- Branching Concepts: Brainstorm key concepts related to the theme and create branches emanating from the center.
- Sub-Branches: Further subdivide branches into more specific concepts, creating a detailed and interconnected structure.
- Visual Aids: Utilize colors, icons, and images to enhance clarity and visual appeal.
4. What are some tools for creating cyber security mind maps?
There are numerous tools available for creating mind maps, both online and offline. Some popular options include:
- XMind: A powerful and versatile mind mapping software with a wide range of features.
- MindManager: A professional-grade mind mapping tool designed for complex projects.
- FreeMind: A free and open-source mind mapping software with a user-friendly interface.
- Lucidchart: An online diagramming tool that offers a range of templates and features for creating mind maps.
- Google Drawings: A free online drawing tool that can be used to create basic mind maps.
5. What are some best practices for using cyber security mind maps?
- Regularly Update: Keep your mind map up-to-date by incorporating new information about threats, vulnerabilities, and security controls.
- Share and Collaborate: Share your mind map with relevant stakeholders to foster communication and collaboration.
- Use it for Training: Leverage your mind map to create engaging and informative training materials for employees.
- Focus on Actionable Insights: Ensure your mind map provides actionable insights that can be used to improve security posture.
Tips for Creating Effective Cyber Security Mind Maps
- Start with a Clear Objective: Define the specific purpose of your mind map to guide its structure and content.
- Keep it Simple and Concise: Avoid overwhelming complexity by focusing on key concepts and using clear and concise language.
- Use Visual Cues: Employ colors, icons, and images to enhance clarity and visual appeal, making the information more engaging and memorable.
- Prioritize Key Concepts: Emphasize the most critical elements by using larger fonts, bolder colors, or strategically placed icons.
- Encourage Collaboration: Involve relevant stakeholders in the mind mapping process to ensure a shared understanding and collaborative approach.
Conclusion: Navigating the Future with a Cyber Security Mind Map
In the ever-evolving landscape of cyber security, a comprehensive and structured approach is essential for effective risk management and proactive defense. Cyber security mind maps provide a powerful framework for visualizing the complex interplay of threats, vulnerabilities, and countermeasures. By leveraging the benefits of mind mapping, organizations can enhance their security posture, optimize their risk management strategies, and navigate the future of cyber security with confidence.
The visual nature of mind maps facilitates clear communication, promotes collaborative decision-making, and empowers organizations to effectively educate their workforce on cyber security awareness and best practices. By adopting this dynamic and adaptable approach, organizations can stay ahead of the curve in the ongoing battle against cyber threats.


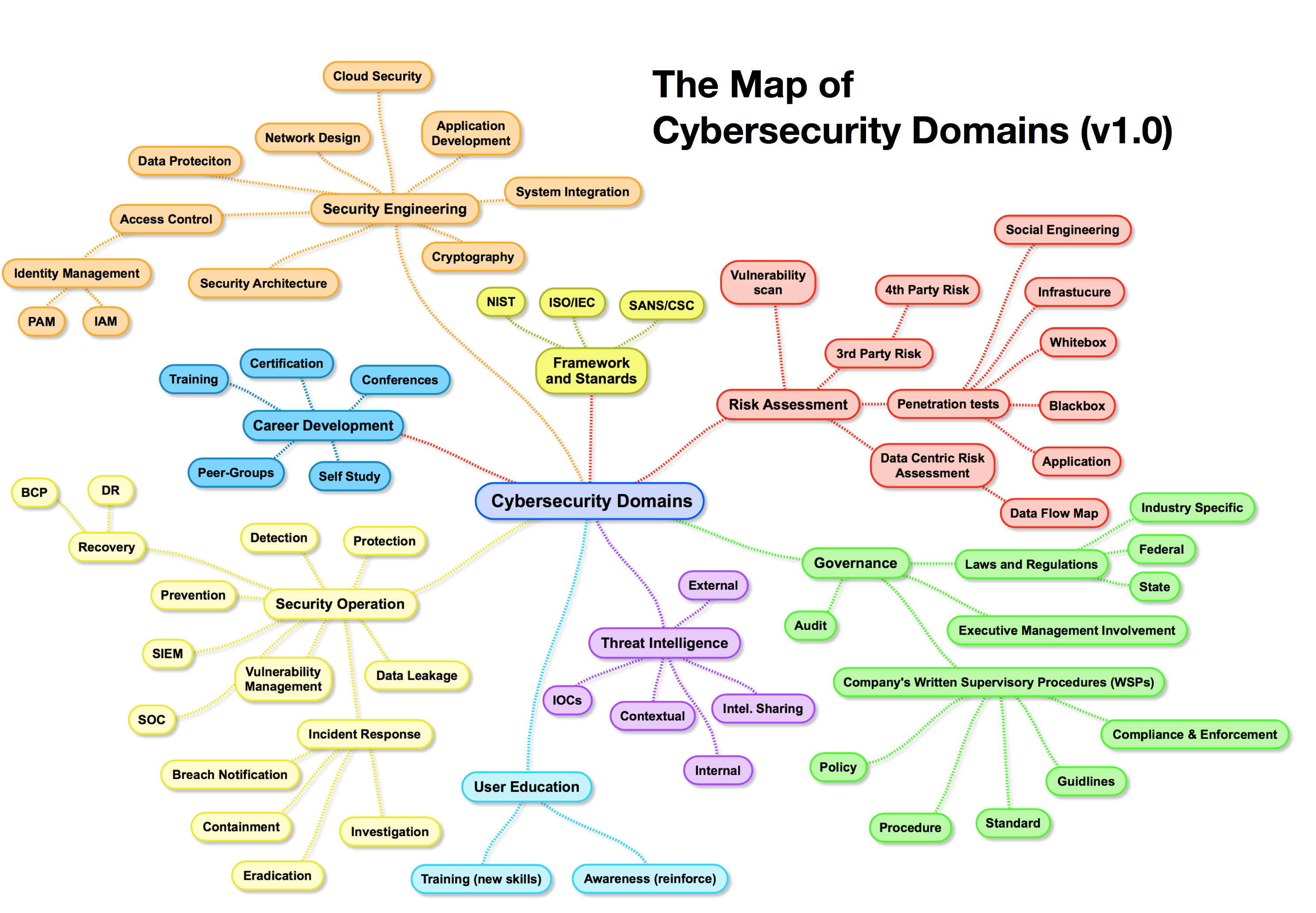



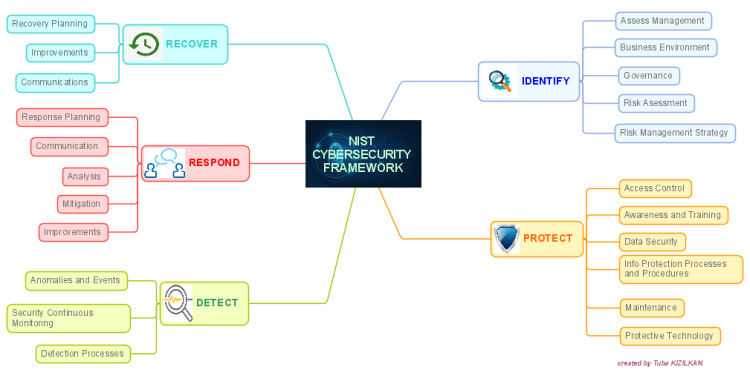
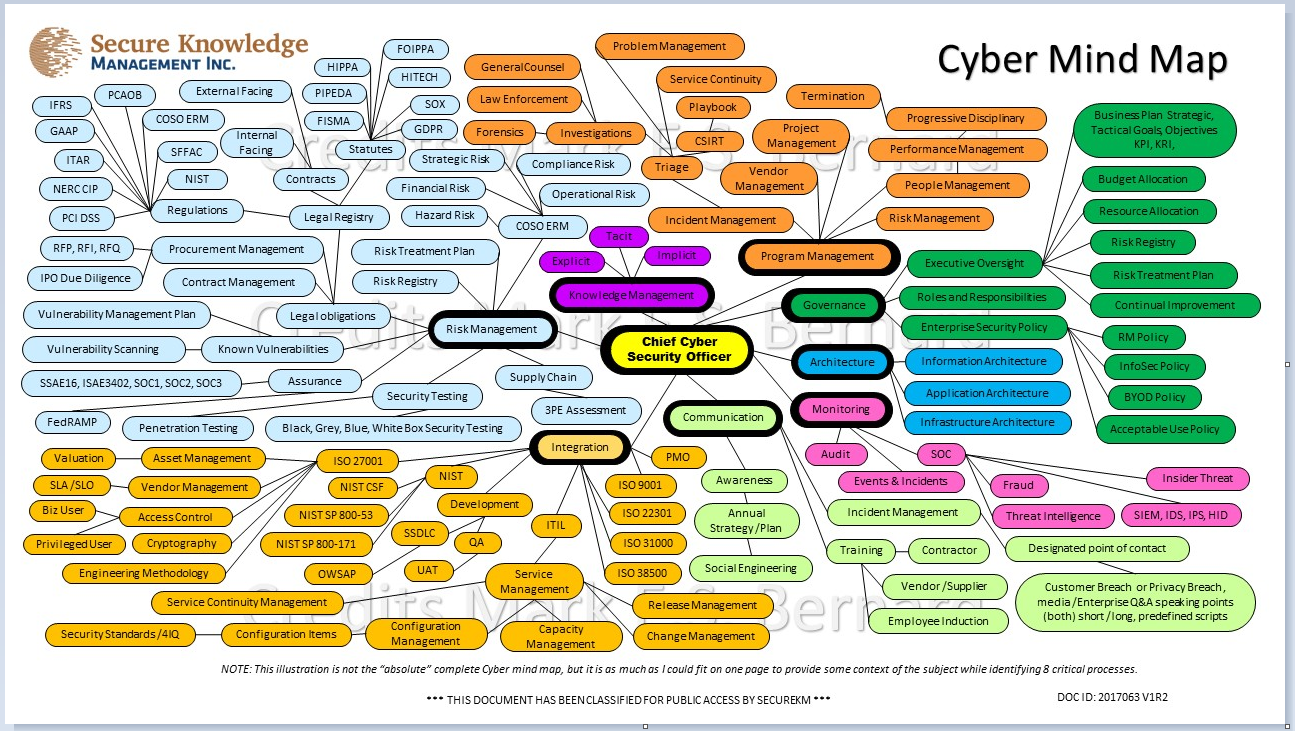
Closure
Thus, we hope this article has provided valuable insights into Navigating the Labyrinth: Understanding the Power of Cyber Security Mind Maps. We hope you find this article informative and beneficial. See you in our next article!